Which of the Following Is an Example of Two-factor Authentication
Which of the following is an example of two factor authentication cisco. A Smart card and personal identification number PIN B Personal identification number PIN and password.
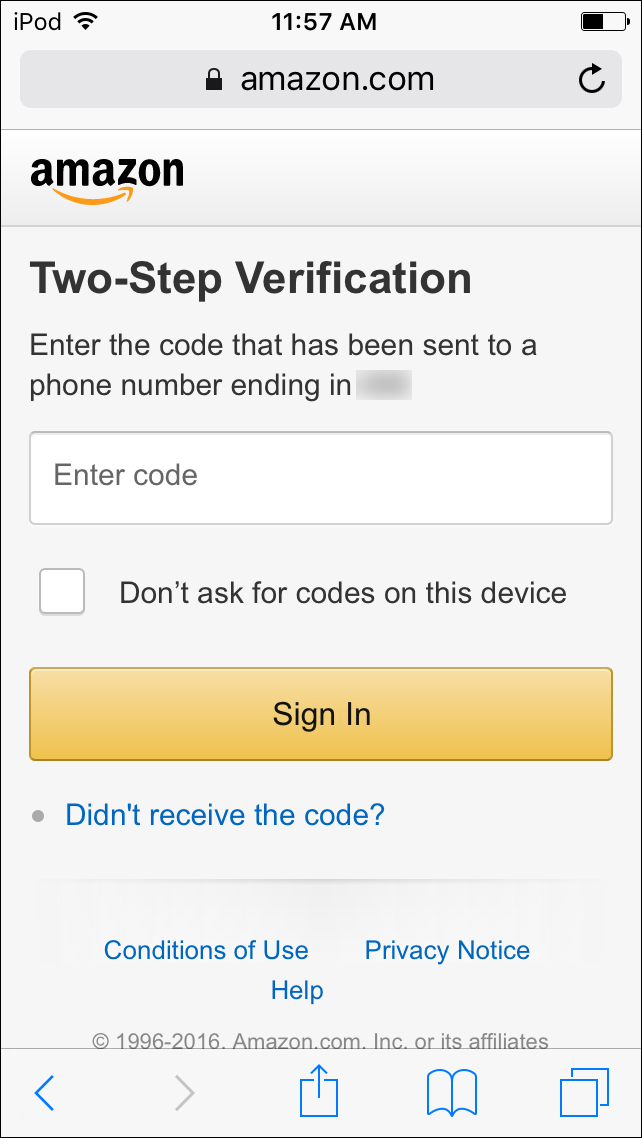
Two Factor Authentication How It Works And Why You Should Use It The Mac Security Blog
Multiple usernamespasswords for all websites Usernamepassword fingerprint scanner and key fob.

. Which of the following is not an example of two-factor authentication. Smart cards and biometrics is an example of two-factor authentication. Two-factor authentication makes the user provide a password and one example of it is the personal identification.
The most popular example of this would be your password to your username. Using a security device with your password to gain access to Internet Banking. A token device and a PIN B.
Multiple usernamespasswords for all websites. Password and hardware token OTP. Which of the following is an example of two factor authentication cyber awareness.
Select the two best answers Authorization. Seenagape August 29 2014. Most other current web-based user authentication systems described as two-step verification also qualify as two-factor authentication.
Which of the following is an example of two factor authentication 2022. D Token and smart card. Magnetic stripe card and an ID badge.
A good example of two-factor authentication is the withdrawing of money from an ATM. Two factor authentication factors enabling checklist. Which of the following is an example of two factor authentication.
Which of the following is an example of two-factor authentication when accessing a virtual server. A username and a password C. A fingerprint and a retina scan.
Password device certificate and PIN B. The type of authentication can vary but will generally be a username and password. The mathematical algorithm used by HMAC-based One-Time Passwords HOTP relies on two types of information to generate a new password based on the previously generated password.
SSL web server certificate and password C. SSO single sign-on enables users to access multiple servers and multiple resources while entering their credentials only once. Which of the following is an example of two-factor authentication.
Using PINs passwords and security questions in any combination is single-factor authentication because all three are knowledge-based. Of the following what two authentication mechanisms require something you physically possess. This functions like a.
Which of the following is an example of two-factor authentication when accessing a virtual server. Which one of the following is an example of two-factor authentication. Googles 2-Step Verification service for example involves the usual password something the user knows and a code sent to the users device something the user has.
Retina scan and a palm print. A pass phrase and a PIN D. Password and Completely Automated Public Turing test to tell Computers and Humans Apart.
Fingerprint and a smart card. Smart card and personal identification number PIN Authentication using smart cards and PINs is two-factor authentication because it combines ownership and knowledge. Which of the following is an example of two factor authentication.
Only the correct combination of a bank card something the user possesses and a PIN something the user knows allows the transaction to be carried out. This is an example of two-factor authentication. PIN Number and Birth Date.
Googles Gmail has a security feature where it can send you a password reset link to an alternate email address if youve forgotten your password. QUESTION 76 Which of the following is an example of two factor authentication A from HISTORY 125 at Technical University of Cluj-Napoca. Vpn is short for virtual private network.
Which of the following is an example of two-factor authentication. VPN is short for virtual private network. Smart card and personal identification number PIN Authentication using Smart card and personal identification number PIN is an example of two-factor authentication because is involves a combination of both ownership and knowledge.
User password and administrator password D. Which of the following is an example of two factor authentication. Which of the following is an example of two-factor authentication.
A device which is synchronized to an authentication server uses which type of authentication. PIN Number and Birth Date. Usernamepassword fingerprint scanner and key fob.
C Password and security questions. Which of the following is the final step a user needs to take before that user can access domain resources. What is an example of two factor authentication.
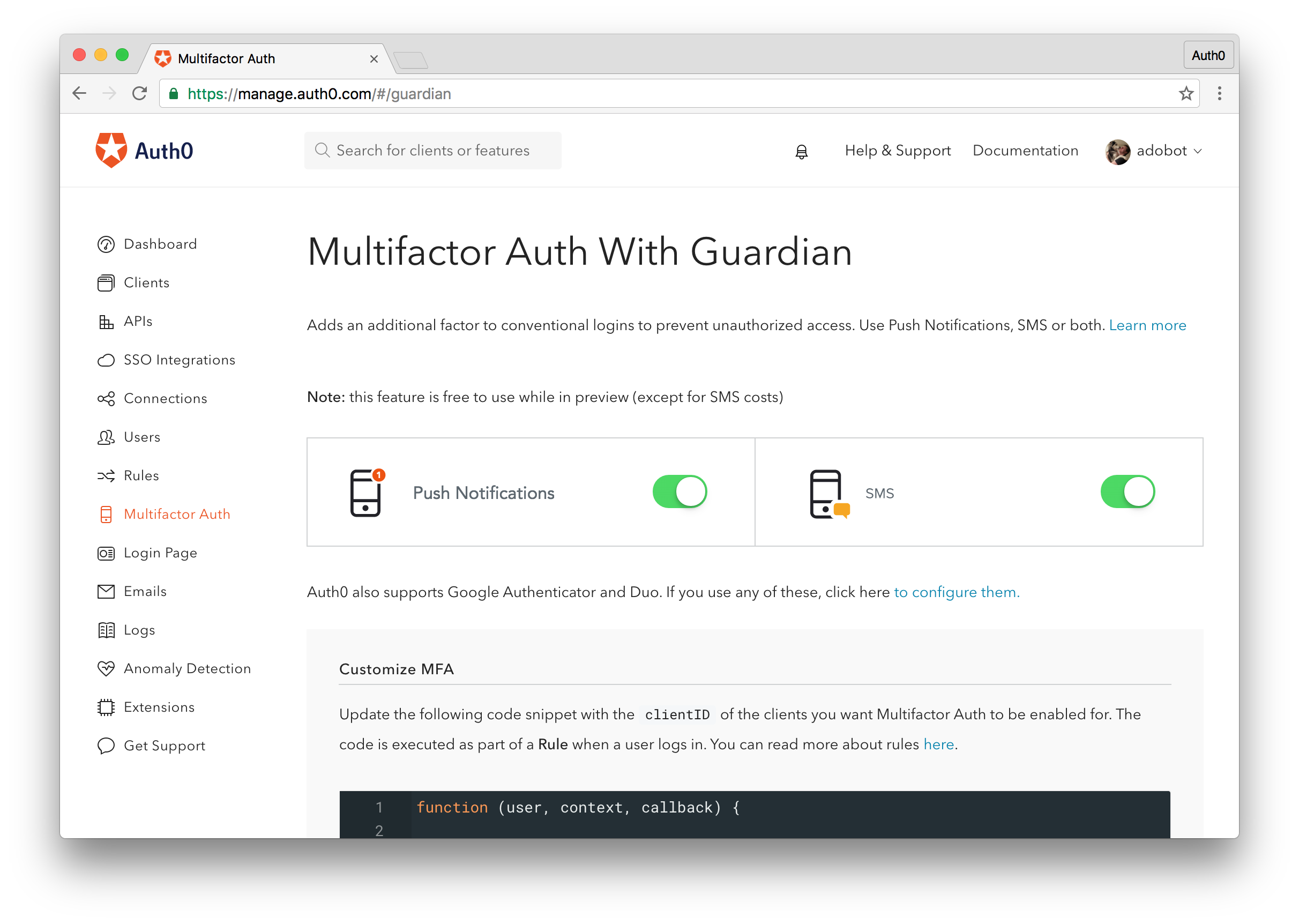
Two Factor Authentication 2fa Auth0

Traditional Two Factor Authentication Vs Beyond Identity S Passwordless Authentication Beyond Identity
Enabling And Disabling Two Factor Authentication Fastly Help Guides

Back To Basics Multi Factor Authentication Mfa Nist

What Is Two Factor Authentication 2fa And Why Should You Use It

How Does Two Factor Authentication Work

8 Apis For Two Factor Authentication Nordic Apis
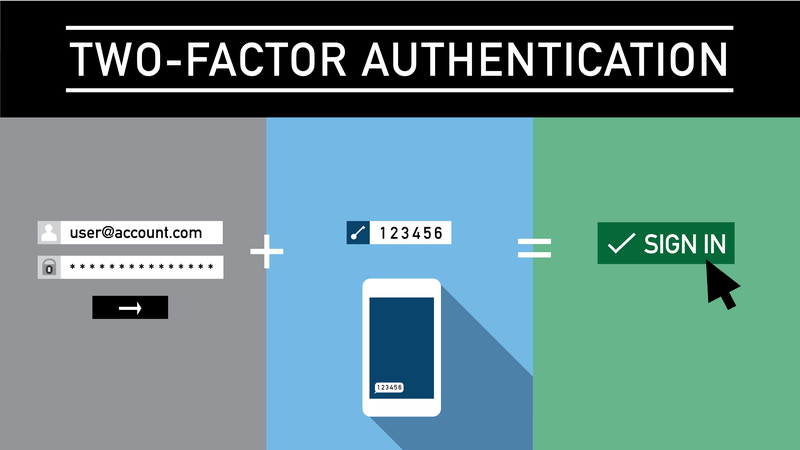
Two Factor Authentication For Beginners By Martin Shelton Medium
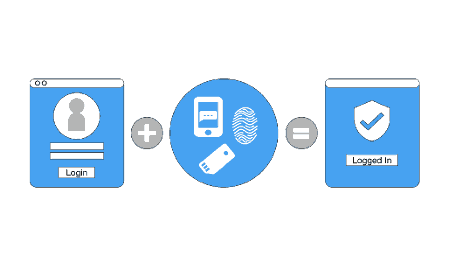
Using Multi Factor Authentication For Network Security

Two Step Login Verification Egnyte

Defining Multi Factor Authentication What It Is And Why You Need It Now Avatier
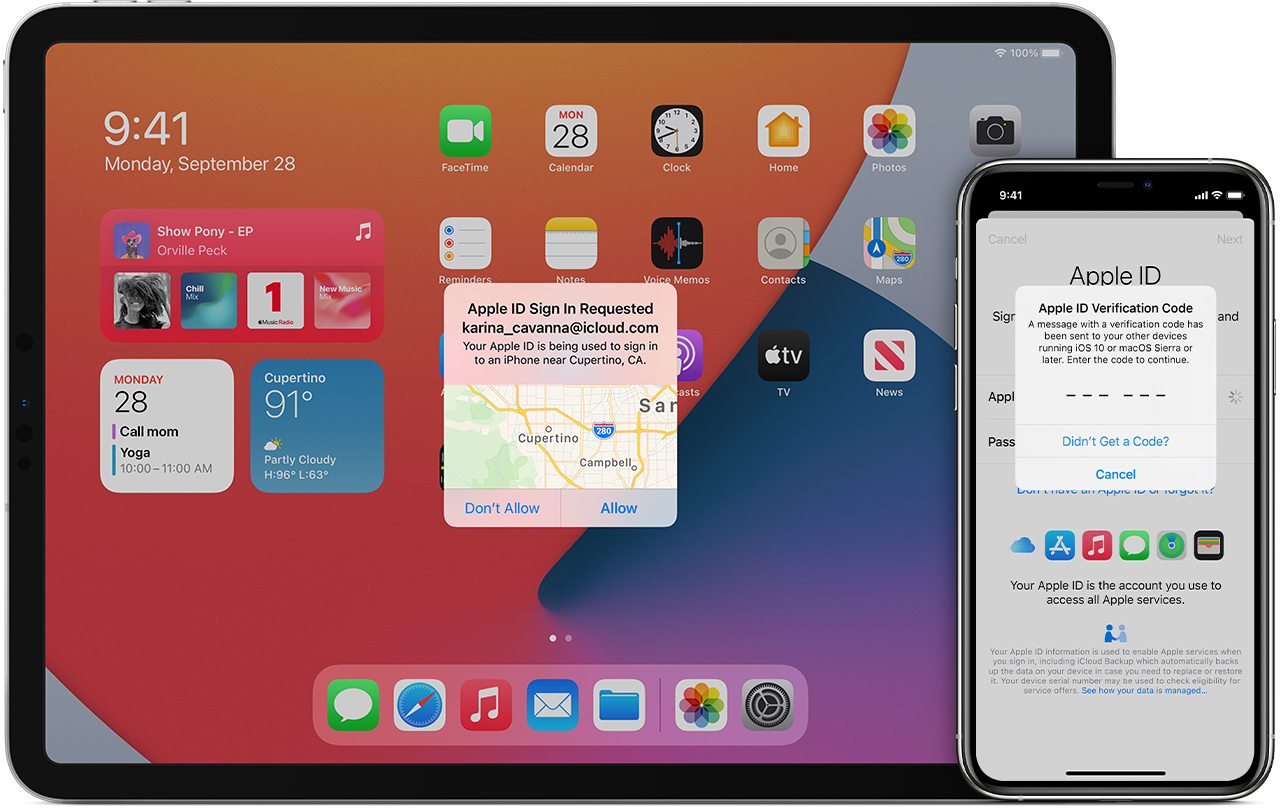
Two Factor Authentication For Apple Id Apple Support Ca
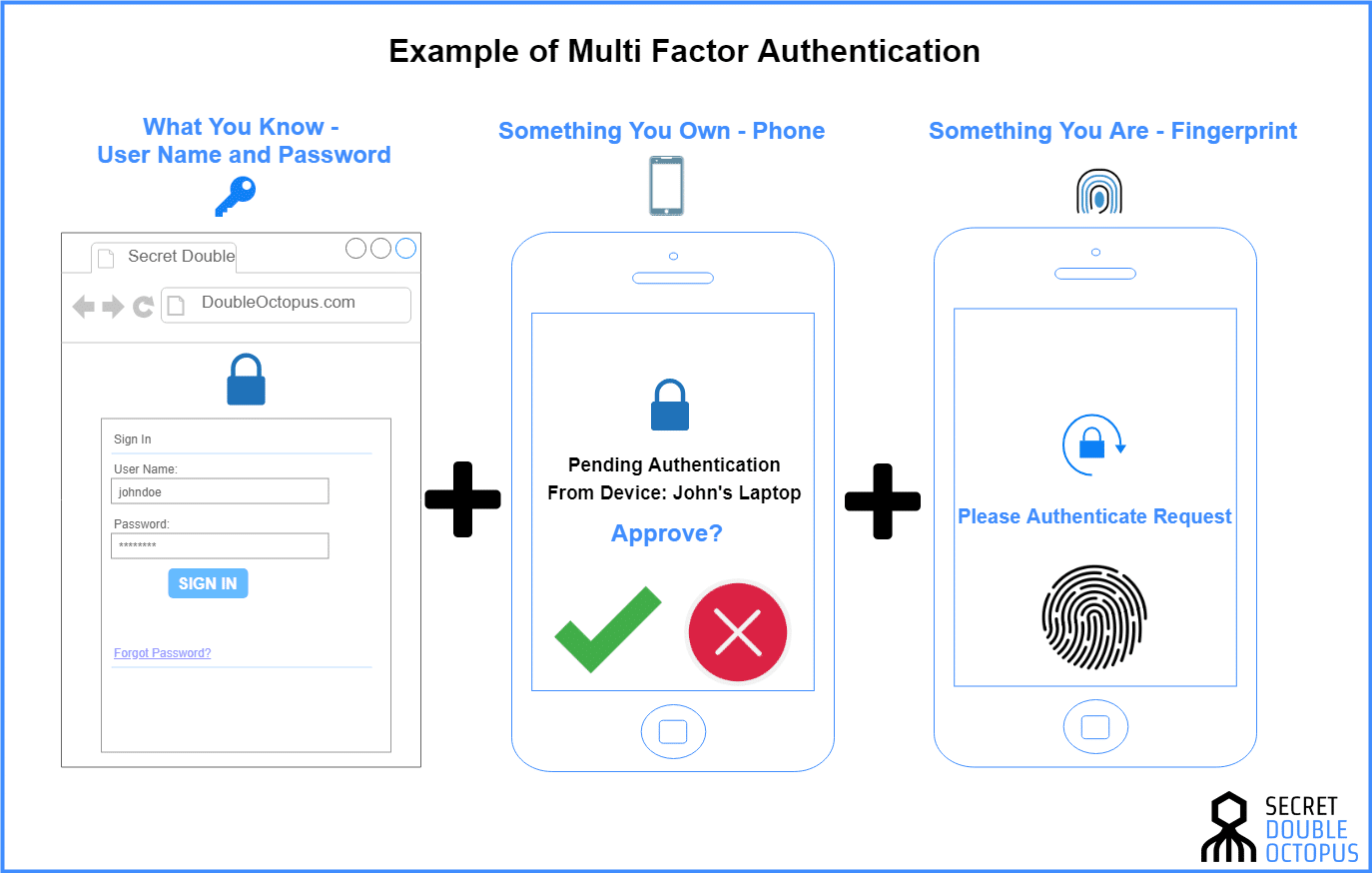
What Is Multi Factor Authentication Mfa Explained Security Wiki

Two Factor Authentication 2fa Data Insights Client Center
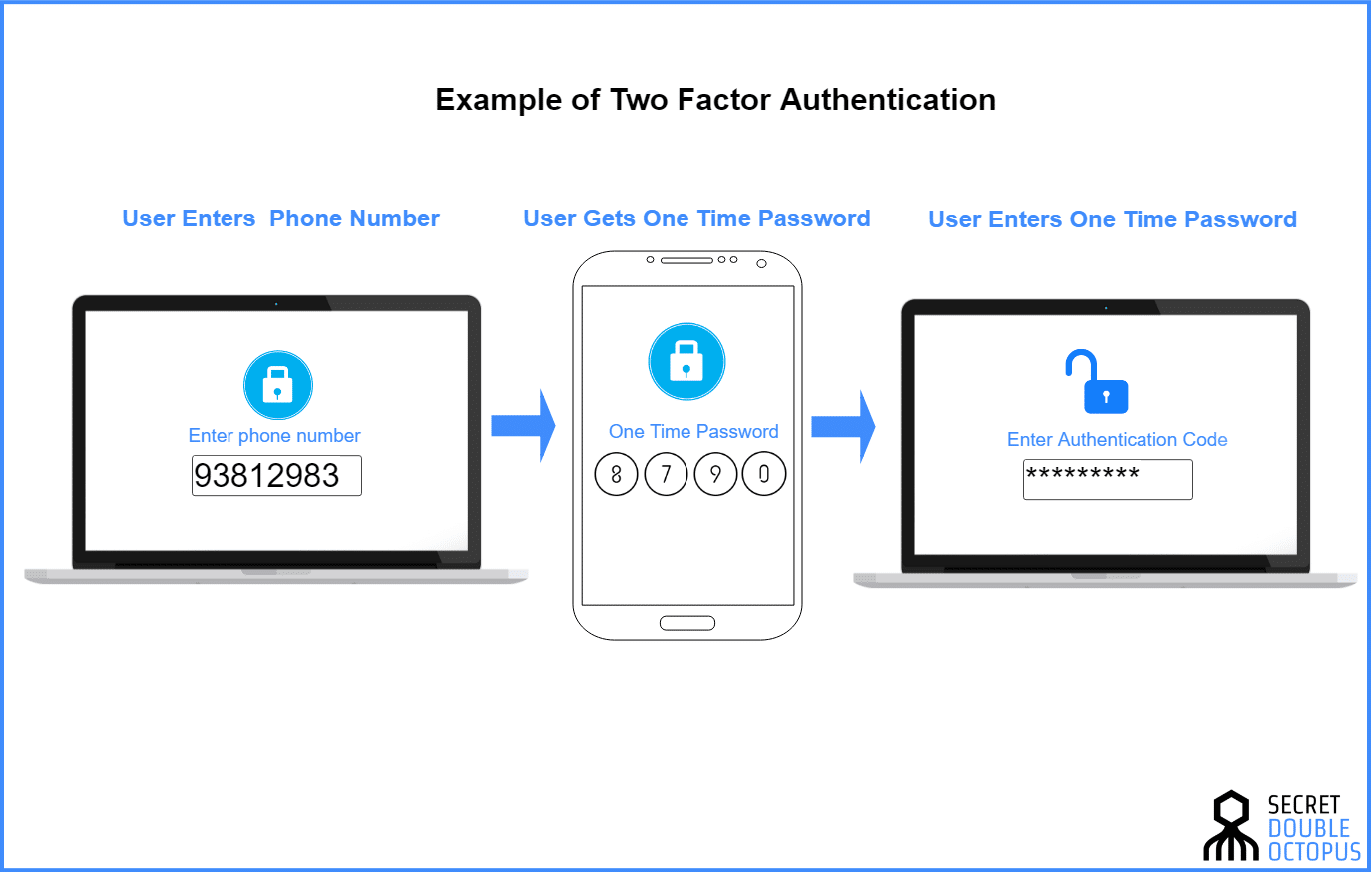
What Is Two Factor Authentication 2fa Security Wiki
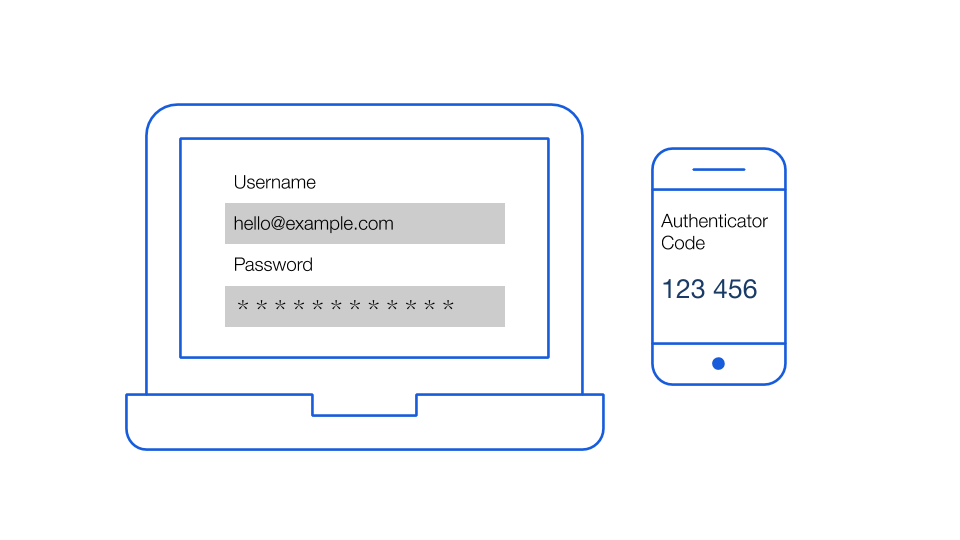
Basics Of Two Factor Authentication With Bitwarden Bitwarden Blog

Cybersecurity 101 Two Factor Authentication Can Save You From Hackers Techcrunch


Comments
Post a Comment